Guest User Access and External Sharing in Microsoft Teams and Office 365
Download this AvePoint eBook to learn how to develop and enforce the right external user access policy for your organization.
Configure your collaboration tools to be effective and secure.
Microsoft Teams has become the central productivity hub for organizations today. Its value in enabling business continuity and collaboration can be seen in a nearly 500 percent increase in daily active users since the start of the COVID-19 pandemic. Now, it is possible to securely allow Microsoft teams guest access, with outsiders participating as members Microsoft Teams can be securely configured to enable outsiders to participate as guest members of a Teams workspace, enjoying and many of the enjoy many of the same functions that insiders use.
This eBook will dive into Microsoft Teams governance and policy considerations that you need to make when creating and managing guest adding external users to Microsoft Teams, user access to your Teams network, as well as the different layers of guest access and the common challenges that accompany a more complicated Microsoft 365 infrastructure. And finally, the eBook will outline some of the major decisions points across four general-purpose guest access policy scenarios for how an organization can set this up with standard licensing.
Learn answers to key consideration questions like:
- Who should be allowed to be invited as a guest?
- What type of guests should be able to access files in SharePoint and OneDrive?
- How should guests be offboarded?
- How should you determine who has access to sensitive information in your environment?
Table of Contents
Introduction
Policy Considerations and Cheat Sheet
The Layers of Guest Access & Common Challenges
Configuring Your Guest Access Policy
Conclusion
Get a Sneak Peek:
Solutions in Practice - AvePoint's Cloud Governance
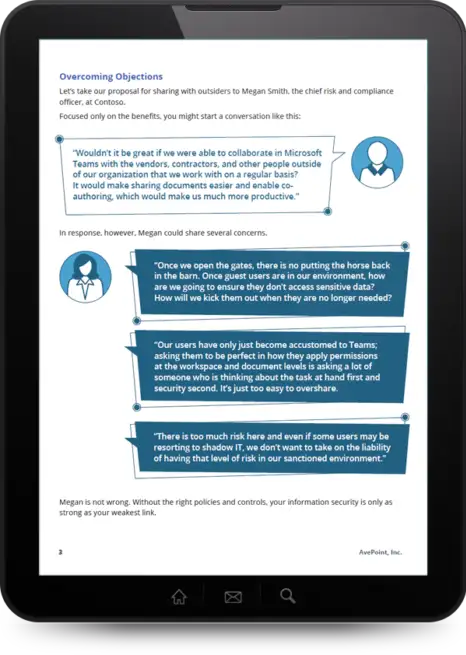
These automated processes allow organizations to scale guest access to Teams in a secure way. After all, the answer to, "should guests be allowed in a Team?" is almost never "yes" or "no," but rather "it depends." - Page 15
Key Takeaways - Establishing a Secure Foundation
Sharing with outsiders requires working through a labyrinth of settings and admin centers. It is best to start by determining your governance policies. Otherwise, it's easy to get lost. - Page 29
Your free guide to creating a secure external sharing policy for your organization.
